Incident Response Planning for Small Businesses
Create an effective incident response plan to minimize damage and recover quickly from security breaches.
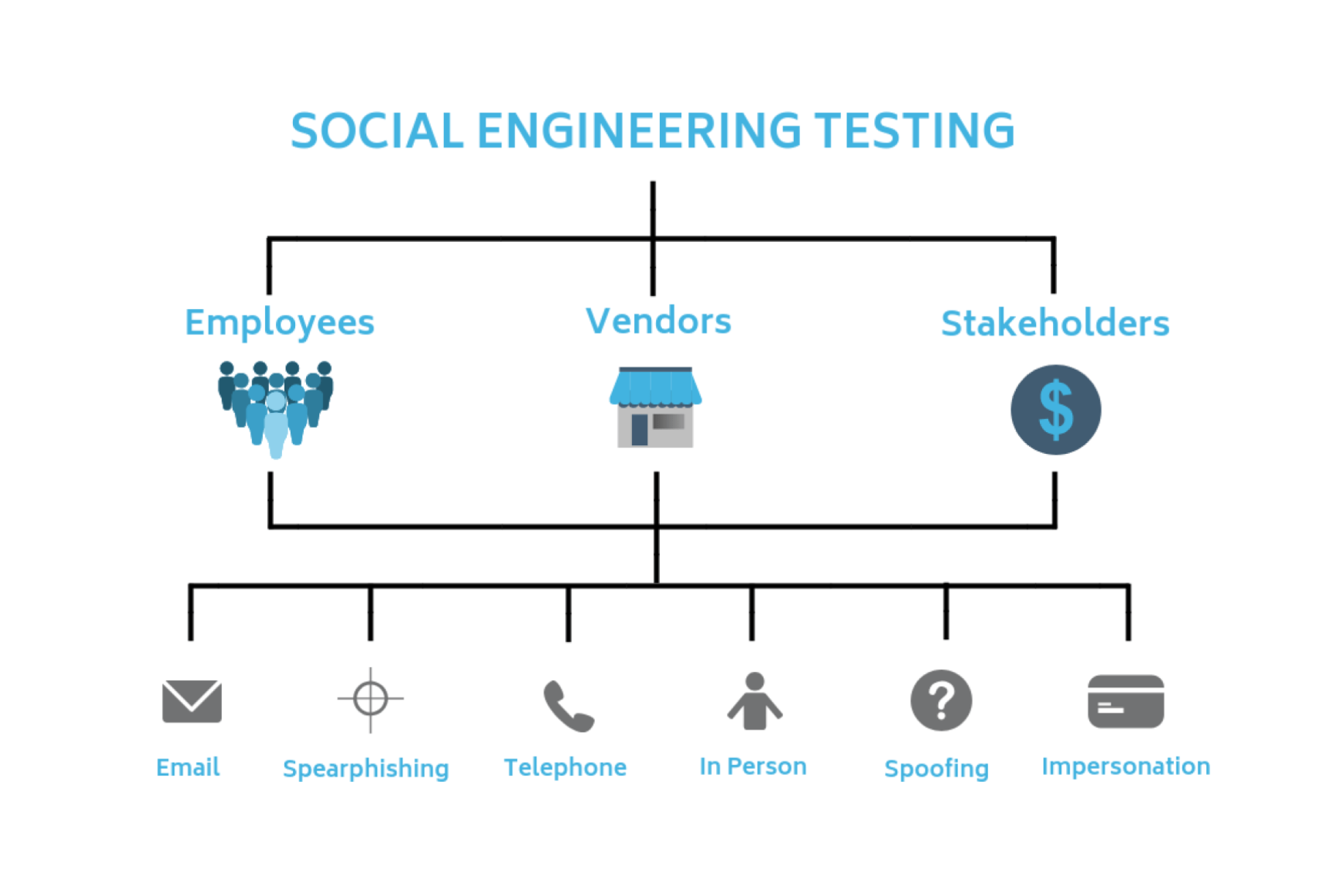
Cyber incidents are not a matter of if, but when. For small businesses, the impact of a security breach can be particularly devastating, with studies showing that 60% of small companies go out of business within six months of a cyberattack. Having a well-prepared incident response plan can mean the difference between a minor disruption and a business-ending catastrophe.
Understanding the Incident Response Lifecycle
Effective incident response follows a structured approach that ensures rapid detection, containment, and recovery while minimizing business impact and preventing future incidents.
The Six Phases of Incident Response:
1. Preparation
Building the foundation for effective incident response through planning, training, and resource allocation.
2. Identification
Detecting and analyzing potential security incidents to determine if they pose a real threat.
3. Containment
Isolating the incident to prevent further damage while preserving evidence for investigation.
4. Eradication
Removing the threat from the environment and addressing vulnerabilities that enabled the incident.
5. Recovery
Restoring affected systems and services to normal operation while monitoring for signs of recurring issues.
6. Lessons Learned
Conducting post-incident reviews to improve future response capabilities and prevent similar incidents.
Building Your Incident Response Team
Core Team Roles:
Incident Commander
Technical Lead
Communications Lead
Business Lead
For Small Businesses:
Many small businesses may not have dedicated personnel for each role. In these cases, individuals may wear multiple hats, but it's important to clearly define responsibilities and ensure adequate coverage.
Essential Components of an Incident Response Plan
Contact Information and Communication Procedures
Internal Contacts:
External Contacts:
Incident Classification and Prioritization
Severity Levels:
Critical (P1):
High (P2):
Medium (P3):
Low (P4):
Response Procedures and Playbooks
Common Incident Types and Response Actions:
Malware/Ransomware:
1. Immediately isolate affected systems from the network
2. Preserve system state for forensic analysis
3. Assess the scope of infection and data impact
4. Activate backup and recovery procedures
5. Coordinate with law enforcement if required
6. Implement additional monitoring and controls
Data Breach:
1. Contain the breach and secure affected systems
2. Assess the type and volume of compromised data
3. Determine legal and regulatory notification requirements
4. Prepare customer and stakeholder communications
5. Implement credit monitoring services if applicable
6. Conduct thorough investigation and remediation
Phishing Attack:
1. Identify and isolate compromised accounts
2. Reset passwords and revoke access tokens
3. Scan systems for signs of unauthorized access
4. Review email logs and security controls
5. Provide additional user training
6. Enhance email security filtering
System Compromise:
1. Isolate affected systems and preserve evidence
2. Analyze attack vectors and methods used
3. Assess data access and potential exfiltration
4. Remove malicious software and unauthorized access
5. Patch vulnerabilities and strengthen controls
6. Monitor for signs of persistent threats
Business Continuity and Recovery Planning
Critical System Inventory:
Backup and Recovery Procedures:
Documentation and Evidence Collection
Incident Documentation:
Legal and Regulatory Considerations:
Testing and Training
Regular Exercises:
Tabletop Exercises:
Technical Drills:
Training Programs:
Post-Incident Activities
Immediate Post-Incident:
Long-term Follow-up:
Measuring Incident Response Effectiveness
Key Performance Indicators:
Response Metrics:
Improvement Metrics:
Continuous Improvement:
Legal and Regulatory Considerations
Notification Requirements:
Evidence Preservation:
Insurance Coordination:
Having a comprehensive incident response plan is not just about technology—it's about people, processes, and preparation. The most successful incident response efforts combine thorough planning, regular testing, and continuous improvement to build organizational resilience against cyber threats.
Small businesses may feel overwhelmed by the complexity of incident response planning, but starting with basic procedures and gradually building capabilities over time is better than having no plan at all. Remember, the goal is not to prevent all incidents, but to minimize their impact and learn from each experience to strengthen your defenses.
Related Articles

Essential Cybersecurity Practices for Small Businesses
Discover the fundamental cybersecurity measures every small business needs to implement to protect against modern threats and data breaches.

How to Protect Your Business from Phishing Attacks
Learn to identify and defend against phishing attempts that target your employees and sensitive business data.
The Complete Guide to Password Security
Master password best practices, two-factor authentication, and password management for enhanced security.
Need Expert Cybersecurity Guidance?
Our security professionals are here to help protect your business. Get a free consultation and vulnerability assessment.
